August 2024
Cybersecurity
Table of Contents



Everyone Wants Your Data
It isn’t the most eye-catching choice, but it would not be out of line to make “data” the word of the year. Our information—from more obvious things like social security numbers and banking information to our shopping habits and how we spend our leisure time—may be the most valuable asset we hold in modern times.
Businesses want to build profiles so they can better target their key customers. The government wants to track population changes. And, of course, the more nefarious actors want to steal your information, or hold it for ransom, to make a quick profit.
And, unfortunately, the healthcare and financial industries are some of the most sought-after targets for cybercrime.
Security training can feel tedious (though many of us at ProAssurance are anxiously awaiting season six of The Inside Man from our security training provider), but with the myriad of news stories about cyber hacks that have occurred recently, it’s easy to see why constant vigilance is needed.
In this issue, we have gathered a variety of resources from ProAssurance’s team, as well as our strategic partners at Tokio Marine HCC. We hope you find these useful, both for your own use and sharing with your clients as part of your outreach.

From the earliest idea of electronically maintaining patient data in the 1960s, through the development of the first electronic health record (EHR) in 1972, to today’s connected devices and web-based systems, the digital healthcare practice has evolved to provide increased convenience, improved patient care, and lower costs to medical providers. But this electronic access to medical records also brings with it additional risks and obligations to practices.
Before the EHR, the biggest threats to securing medical records were likely fires, water damage, or an unauthorized person getting the keys to the records room. With the growth of the digital practice, the threat is both more varied and more difficult to defend against. Cyberattacks have put sensitive patient data at risk of exposure and the practice at risk of violating state and federal regulatory and privacy laws. Worse, a cyberattack can also put patient care and safety at risk.1
The Patient Safety Impact of Cyberattacks
Any device or system that is connected to the internet is vulnerable to attack and compromise by a determined and knowledgeable attacker. This vulnerability can put healthcare business revenue, patient privacy, and even patient safety at risk. A few recent examples:
- A large scale phishing attack in October 2020 affected six hospitals in the University of Vermont (UVM) Health System resulting in postponed appointments, scheduling problems, delayed chemotherapy and radiation treatments, and weeks-long delays to determine whether cancer biopsies were malignant. The attack began when an unwitting employee on vacation opened a personal email on his work laptop and opened an attachment. The email was from a legitimate local business that had been hacked. When the employee returned and logged into the hospital network, the attackers launched the malware.
- In 2021, researchers at McAfee discovered five vulnerabilities in infusion pumps from B. Braun (one of the largest infusion pumps vendors) that could have enabled attackers to conduct remote network attacks or remotely deliver dangerous levels of medication to patients.
- In February 2024, attackers accessed an unsecured computer server used by Change Healthcare. The attack cut off providers from billions of dollars of revenue, disrupted service at pharmacies across the U.S., and may have compromised the personal data of a third of Americans.
- In early May 2024, attackers staged a ransomware attack on Ascension after an employee unknowingly downloaded a malicious file, enabling the attackers to block access to patient medical records, forcing staff to rely on paper and manual processes to order medical procedures, communicate across separate departments, and keep track of hospital patients’ evolving conditions.
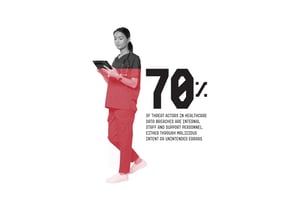
These attacks are not rare and often come from unexpected sources. The employee at UVM who unwittingly launched a ransomware attack, for example, is not alone. The Verizon Business 2024 Data Breach Investigations Report revealed that 70% of threat actors in healthcare data breaches are internal staff, contractors, and support personnel—the highest percentage of the 10 industries studied. A bit of comfort can be taken to know that approximately half of all healthcare breaches were miscellaneous errors, not malicious intent. That means a strong employee cybersecurity awareness campaign in a healthcare organization could dramatically reduce the incidence of successful attacks.



Cyberattacks in Healthcare: Widespread and Costly
When thinking of ways that a cyberattack could affect a healthcare organization, ransomware attacks and data theft likely come immediately to mind for most people because they make headlines. While these are among the most prevalent cyber risks in the healthcare industry, another critical risk is hiding in plain sight: connected medical devices. These ubiquitous IV pumps, blood pressure monitors, EKG machines, and other devices are connected to a practice’s network and often to the internet to store and back up data to cloud services. The statistics are troubling:
- 79% of medical devices in hospitals are used regularly, making them difficult to update.
- 53% of connected devices contain critical vulnerabilities that could jeopardize patient care, safety, or confidentiality.
- 73% of IV pumps in hospitals contain critical vulnerabilities that could jeopardize patient care, safety, or confidentiality.
Connected Medical Devices: Threats Hiding in Plain Sight
“Think of IT security as a chronic illness, a condition that requires ongoing treatment, testing, and re-evaluations. With security, the goal is not an outright cure but a lessening of symptoms, a lowering of risk.”2
In the first half of 2024, the breaches reported to the U.S. Department of Health and Human Services, Office of Civil Rights, affected 45.5 million individuals. That number already eclipses the total for all of 2020 by 30% and (on a prorated basis) will eclipse three of the previous four years. Furthermore, a 2023 study revealed that healthcare organizations experienced an average of 40 cyberattacks in the prior 12 months—88% had at least one.1 The same study revealed that 77% of supply chain attacks, 69% of email/spoofing phishing attacks, 68% of ransomware attacks, 49% of cloud service compromise, and 43% of data loss or exfiltration incidents impacted patient safety and care.1 Despite these threats to patient safety and the $10.93 million average cost of healthcare cyberattacks, only 51% of organizations plan to increase investments in cybersecurity after a breach.
Cyberattacks that block access to patient records, paralyze critical medical devices, and impact patient care are not just an “IT problem” best left to tech experts—they are a patient safety issue. The good news is—because about half of all healthcare data breaches are caused by employee errors—there is an opportunity for a practice to build a pervasive “culture of cybersecurity” and prevent data breaches with a strong program of employee training and awareness. Providers work hard at building a “culture of patient safety” in their practice. Applying that same diligence to building a “culture of cybersecurity” can help employees become aware of their role in guarding against inadvertent cybersecurity incidents and mitigate cyberattacks in general.
1. Ponemon Institute, Cyber Insecurity in Healthcare: The Cost and Impact on Patient Safety and Care 2023, data cited from the full report.
2. Daniel Berger, President and CEO of cybersecurity consultants Redspin, quoted by Diana Manos, “5 Ways to Avoid Health Data Breaches,” Healthcare IT News, February 19, 2014.
In an era when technology is integral to medical practice, the stakes for cybersecurity are higher than ever. Healthcare facilities’ dependency on EHRs, large amounts of sensitive personal health information (PHI) data, and the critical need for continuity of care render the healthcare industry highly vulnerable, according to a recent study by the U.S. Department of Health and Human Services. Safeguarding these digital assets is not just a matter of regulatory compliance but a critical aspect of medical professional liability insurance.
The Growing Threat of Cyberattacks
The increasing frequency and severity of cyberattacks highlight a growing vulnerability. According to Jonathan Whitman, ProAssurance Vice President, Claims Reinsurance Liability and Analytics, “It’s not a question of if, but when a breach will occur.”
With the sheer volume of attacks and evolving tactics, including ransomware and phishing, the risks are significant. Recent high-profile incidents, such as the Colonial Pipeline attack in 2021 that led to fuel shortages and higher gas prices in several states, underscore the potential for widespread disruption. These attacks, regardless of industry, can lead to significant operational downtime. In healthcare, where EHRs are crucial, a breach can render access to patient data impossible, halting treatment and disrupting patient care.
Contractual Considerations and Coverage Gaps
Understanding your insurance policy is critical, especially regarding vendors and third-party entities. Many policies may not cover them, which could lead to gaps in coverage if these parties are compromised. “Be sure to read the contracts carefully,” advises Whitman. “Third-party vendors that provide services such as EHRs or billing are often not covered under their MPL policy, so it’s vital to understand what is and is not included.”
Some third-party contracts specifically disclaim any damages sustained as a result of their actions/inactions, which would mean they would not reimburse for any costs or losses incurred as a result of those actions/inactions.
However, healthcare and hospital organizations are urging that a federal cybersecurity reporting proposal explicitly cover insurers and third-party vendors, especially in light of the significant cyberattack on Change Healthcare, a medical claims clearinghouse. The proposed rule, introduced by the Cybersecurity and Infrastructure Security Agency (CISA) earlier this spring, mandates that companies in critical infrastructure sectors report cyber incidents within 72 hours of discovery and document any ransom payments within 24 hours. Despite this, CISA has chosen not to include sector-specific reporting requirements for insurance companies, health IT providers, or labs and diagnostic facilities. The American Hospital Association has contended that this omission is problematic, arguing that the disruption to one company can have widespread repercussions across the entire industry.
Whitman advises that insureds store copies of third-party vendor contracts in a place where they can retrieve them should they have a compromise of the computer system. “If you are the victim of a ransomware attack and cannot get documents out of your computer, having copies stored offsite or in paper form would be very useful,” he said. “These contracts may become very important as part of the insurance coverage determination.”
Act Fast to Minimize Impact
When faced with a cyberattack, one aspect within our control is the speed at which we file a claim, which can significantly impact the recovery process. Whitman notes there are very specific requirements for reporting a cyber event. In fact, failure to report a cyber claim within the reporting requirements timeframe could result in a denial of coverage.
“Promptly reporting security breaches or ransomware attacks is crucial,” said Whitman. “Just as you would shut off a water leak to prevent further damage, acting swiftly can mitigate the impact of a cyber incident.”
— Jonathan Whitman, VP, Claims Reinsurance Liability and Analytics
He further advises that insureds not attempt to settle a claim on their own. “We’ve had insureds not realize they had coverage for cyber incidents and try to handle the issue themselves, which is a violation of the terms and conditions of the policy/endorsement,” he said.
You will want to include the policy number and relevant details about the insured and policyholder name when filing a cyber claim. Delays often occur when the insured calling in a claim doesn’t know the name the policy was issued under, according to Whitman.
“Simply not having their policy number on hand can waste valuable time,” he said. “The urgency of these claims cannot be overstated—any delay can exacerbate an already bad situation.”
Essential Cybersecurity Measures
Effective cybersecurity is not just about having the latest technology; it’s about fundamental practices that safeguard your data. Here are key measures to follow, for both you and your clients:
- Update Software Regularly: Ensure all software and antivirus programs are up to date. This helps protect against known vulnerabilities.
- Use Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of security beyond just passwords, reducing the risk of unauthorized access.
- Avoid Writing Down Passwords: Store passwords securely using tools like LastPass, and never write them down on easily accessible surfaces.
- Educate and Train Employees: Regular training on recognizing phishing attempts and other cyber threats is essential. Employees are often the first line of defense against cyber threats.
- Backup Data: Regularly back up data to ensure that you can recover it in the event of a breach. Aim to do this at least once a quarter.
Prepare Now for the Inevitable
Cybersecurity threats are a persistent challenge, and preparation is key. This means not only implementing strong cybersecurity measures but also ensuring that your insurance coverage is comprehensive and up-to-date. “In the digital age, where the risk of cyber incidents is ever-present, a proactive approach to both cybersecurity and insurance can safeguard your practice from potentially devastating losses,” said Whitman.
As a trusted agency partner, consider how you handle your important client data as well. “If you were hacked today, what confidential client data could be exposed?” asked Whitman. “Just because you’re not a direct healthcare provider doesn’t mean you don’t have personally identifiable information or personal health information from the claims of your clients. Think about the banking information you may have on file.”
Navigating the intersection of MPL insurance and cybersecurity requires vigilance and preparation. By understanding your policy, promptly addressing claims, and maintaining robust cybersecurity practices, you can better protect your business and your clients from the increasingly sophisticated world of cyber threats.
Cyber liability protection with CyberAssurance Plus is included in certain MPL policies, and expanded cyber coverage is offered through ProSecure. Both are underwritten by Tokio Marine HCC, formerly NAS Insurance Services, LLC.
Cyber claims can be reported directly to the ProAssurance Claims Intake System at ReportClaim@ProAssurance.com or directly to Tokio Marine:
- 818-382-2030 (8 a.m.- 5 p.m. PT)
- 888-627-8995 (after regular business hours, on weekends, or holidays)

Ransomware attacks are increasing in frequency, so healthcare organizations need to be ready to tackle them. By taking these steps, your clients can lessen the likelihood of becoming a target for ransomware and other cyber threats.
1. Train Employees on Phishing and Data Risks
It is essential to train employees to recognize and report phishing attempts. Staff should be educated on what typical phishing emails look like. To ensure effective training, healthcare organizations should use industry-specific scenarios and real-life examples relevant to their field. Common phishing tactics include:
- Impersonated Email Addresses: Emails that appear similar to your organization’s domain name.
- Requests for Personal Information: Messages asking for sensitive data that employees shouldn’t give out before verifying through alternative methods (such as an authenticated phone call or text).
2. Conduct Vulnerability Assessments
Understanding your vulnerabilities is crucial for preventing ransomware attacks. A vulnerability assessment helps identify and address gaps in your cybersecurity. Healthcare organizations should regularly conduct these assessments to uncover potential weaknesses. When conducting a vulnerability assessment:
- Engage a Specialized Third Party: Choose an external provider with expertise to ensure objective and unbiased results.
- Seek Actionable Recommendations: Some providers may offer limited value if they don’t provide clear steps for addressing identified issues.
3. Implement Multi-Factor Authentication
Multi-factor authentication (MFA) enhances security by requiring multiple forms of verification before granting access. This might include a password along with a fingerprint or PIN. Many healthcare organizations do not currently use MFA for email or remote systems, leaving them vulnerable if a single password is compromised. Implementing MFA reduces the risk of unauthorized access and enhances overall security.
4. Encrypt Computers and Data
Encryption is a fundamental component of cybersecurity. It protects data both at rest (stored on computers or servers) and in transit (when transmitted over networks) by converting sensitive information into unreadable formats without the correct key or password. This ensures that even if data is stolen, it remains inaccessible without proper decryption.
5. Backup Critical Data
Regularly backing up data is crucial to defend against ransomware attacks. Backups can be stored on external hard drives, network storage systems, or cloud-based solutions. It’s important to periodically test these backups by restoring them to confirm their reliability.
6. Require Strong Passwords
Strong passwords are a primary defense against identity theft. Ensure passwords are robust and unique for each account to prevent compromise. To enhance password security:
- Use a Password Manager: This tool can generate and store complex passwords for different accounts, minimizing the risk of using the same password across multiple sites.
- Avoid Password Reuse: Different passwords for different accounts help protect sensitive information from being accessed if one account is compromised.
Source: The Cyber Research Databank

Healthcare: A Prime Target for Cyber Threats
The healthcare sector is a particularly vulnerable target for cyberattacks, with hospitals and healthcare facilities operating on numerous interconnected systems and networks, including EHRs, computerized order entry, and practice management software, to name a few. These virtual connections, though they generally work to make modern healthcare more efficient, also facilitate a constant flow of data, including sensitive and private information like health records, billing and account information, social security numbers, and medical research materials. The sharing of data across multiple providers and facilities in a health system creates a widening attack surface for cyber thieves, where a breach to one piece of the network could mean a threat to healthcare operations as well as patient privacy and safety.
Threat actors locate vulnerabilities in an organization’s network, software, or security system and use various tactics like ransomware through remote access technology, or phishing to access, steal, and potentially sell data for financial gain. Medical devices like infusion pumps, remote monitoring bands, and imaging equipment are part of the equation too, with an average hospital room containing 15 to 20 connected devices, sometimes outnumbering even mobile smartphones and laptops. These implements may enable easy entry onto servers, creating a pathway for hackers to reach and penetrate valuable data. An exposure or breach can compromise device functioning, make vital patient information inaccessible to providers, disrupt care plans, and delay lifesaving treatments, posing a significant threat to all stakeholders and eroding trust between patient and provider.
Cyberattacks subject healthcare organizations to potentially devastating legal and financial outcomes as well, negatively impacting the livelihoods and professional reputations of both provider and facility.
A few sobering statistics:
- The average total cost, globally, of data breaches across industries in 2023 was $4.45 million, which represents a 15.3% increase from $3.86 million in 2020 (IBM, Cost of a Data Breach Report 2023).
- Healthcare industry data breaches are the most expensive, costing an average of $10.93 million per breach in 2023, nearly double that of the financial industry at $5.9 million.
State of the Cyber Market: Cyber Loss Trends
ProAssurance partner, Tokio Marine HCC – Cyber & Professional Lines Group (CPLG), a member of the Tokio Marine HCC group of companies based in Houston, Texas, underwrites customized cyber liability coverage solutions to help protect our insureds. They impart cybersecurity expertise through resources and tools designed to help organizations reduce their risk of data breaches, providing online cyber security training, incident response plans, and other information required for both federal and state compliance.
Tokio Marine HCC’s 2023 Cyber Strong® Cyber Report highlights a potential “new record for financially motivated cyber-attacks” and increased cyber losses across industries. Information from this source, along with a few others that narrow the focus to the healthcare industry, underlines the value of comprehensive cyber liability coverage for healthcare entities. Cyber threats are unpredictable, and attackers will take advantage of both practiced and new or developing tactics and techniques to infiltrate or exfiltrate healthcare frameworks. Below are some of the most widely leveraged cyber threats:
Ransomware: A type of malware that “kidnaps” a victim’s sensitive business data, or devices, and holds it hostage until a ransom is paid and access is restored. If no ransom is paid, the victim can lose their data.
According to Tokio Marine HCC’s Cyber Report, ransomware attacks are the main driver of cyber insurance loss when considering all industries. After a surge in 2019, the FBI’s Internet Crime Complaint Center (IC3) report noted a 36% decrease from 2021 to 2023 in the frequency and severity of ransomware attacks. Notably, Tokio Marine HCC aligned with this trend and experienced a 58% decrease in ransomware attacks for the same time period. These drops may be due in part to a heightened awareness for these types of attacks, along with subsequent improvement of security standards at many U.S. organizations, and the requisite cybersecurity controls included in cyber insurance coverages, among other factors. A desire to avoid government attention could explain threat actors shifting the focus to targets outside the U.S, and many ransomware group activities were impeded during the Russia-Ukraine conflict.
Nevertheless, per Tokio Marine HCC’s Cyber Report, ransomware seems resilient and “continues to prove how agile it is in adjusting to security improvements and government actions.” Ransomware levels have recently returned to highs resembling those of just a few years ago. According to FBI estimates, only 20% of ransomware attacks are reported. There is heightened concern about widespread systemic cyber events that result from these types of incidents, like the zero-day file transfer exploits in 2023, the 2024 ransomware attack on non-profit Catholic healthcare system Ascension, and the attack on Change Healthcare, a healthcare payment processor that paid $22 million in ransom payments to hacker group BlackCat. These events had downstream effects that impacted patient care and treatment.
A 2023 independent study of healthcare organizations by Ponemon Institute shows that about 54% reported experiencing, on average, four ransomware attacks in the last two years, with 68% reporting that these attacks had a negative impact on patient treatment and safety. This study also revealed that the number of healthcare organizations paying ransoms decreased from 51% to 40% from 2022 to 2023, though the total amount paid in those years actually increased by 30% (from $771,905 to $995,450).
Business Email Compromise (BEC): This type of fraud occurs when a criminal impersonates a business contact to trick an employee, customer, vendor, etc., into transferring money to that criminal or giving out sensitive information (passwords, address). This is difficult to detect with traditional software tools, as it does not use malware or malicious URLs that could be scanned/analyzed with standard software defense tools. (Tokio Marine HCC: How to Protect Against Email Fraud)
Email fraud, the most common cyber threat to organizations, accounted for 84% of reported cyber incidents in all industries in 2022, according to Tokio Marine HCC’s Cyber Report. Ponemon Institute’s study shows a heightening concern among 62% of participating healthcare organizations for BEC/spoofing phishing incidents, and a similar level of concern about compromises to cloud-based accounts, whereas concern for ransomware dropped to 48%. The frequency of BEC attacks has increased in the past two years to an average of five attacks per organization.
Data Breaches: Any security incident involving unauthorized access with theft of sensitive or confidential information in a system without the knowledge or authorization of the system owner. A cybercriminal, for example, may obtain someone’s credentials using a phishing email technique, then use those credentials to access an organization’s account and steal personal and private data, such as credit card numbers, banking information, or medical records.
Healthcare experiences a significantly high incidence of data breaches when compared to other industries. Facilities struggle with security gaps, unauthorized access, and overlooked areas of vulnerability, despite security implementations and HIPAA guidance. In 2023, records were set in most reported data breaches (725) and also highest number of breached records (over 133 million exposures and unauthorized disclosures), as reported to the Department of Health and Human Services Office for Civil Rights. Also reported was a 239% increase in hacking-related data breaches between January 2018 and September 2023 (79.7% of data breaches in 2023 were from hacking incidents).
Privacy Violations: The Tokio Marine HCC Cyber Report states that the unlawful collection of private information through biometric scanning or website tracking has spurred litigation in recent years. Implementation of Meta Pixel, the website tracker developed by Meta (formerly Facebook) and used on over 30% of the top 100,000 websites, has led to hundreds of class action lawsuits against corporations in the U.S. Healthcare is also impacted, with litigations alleging violations of state and federal privacy laws, with compromised private healthcare information. These cases can take years to reach a settlement or get dismissed and, in the meantime, legal fees grow.
The Value of Cyber Liability Coverage
A comprehensive cyber liability coverage plan offers healthcare entities protection against unpredictable cyber threats like data breaches and viruses, which can lead to theft of information, corrupted assets, interruption or loss of business, and significant regulatory fines or defense costs.
Tokio Marine HCC reviews and analyzes policyholders’ ransomware claims and, through Active Domain Monitoring (ADM) and network scans, studies attack patterns to bring awareness to the most commonly leveraged vulnerabilities, as well as new and evolving threat techniques and tactics utilized by ransomware operators. Tokio Marine HCC advises that “proactive detection and alerting about critical vulnerabilities and exposures in customers’ internet facing assets can substantially reduce the incidence of ransomware attacks.”
Comprehensive coverage, plus an education and awareness of best practices, can help organizations mitigate the risk of future attacks.
Tokio Marine HCC:
Cyber Strong 2023 Cyber Report https://www.tmhcc.com/en-us/news-and-articles/thought-leadership/2023-cyber-report
Cyber & Professional Lines Group https://www.tmhcc.com/en-us/contact-us/underwriting-teams/cyber-and-professional-lines-group
Data Security Risk Resource & HIPAA https://secure.proassurance.com/risk-resource/data-security-risk-resource--hipaa/
*Minimize Your Attack Surface https://pra.nascybernet.com/view_post.php?id=10214
*How to Protect Against Email Fraud https://pra.nascybernet.com/view_layout.php?layout_id=7373
*Training Courses: An informative video library covering the basics of privacy, data breaches, ransomware, fraud, and protecting your information https://pra.nascybernet.com/view_layout.php?layout_id=7502
*Agents can access these Tokio Marine HCC resources using their secure ProAssurance portal log-in.
Ponemon Institute:
Cyber Insecurity in Healthcare: The Cost and Impact on Patient Safety and Care 2023 https://www.proofpoint.com/sites/default/files/threat-reports/pfpt-us-tr-cyber-insecurity-healthcare-ponemon-report.pdf

ProAssurance works in collaboration with Tokio Marine HCC to offer cyber liability insurance for ProAssurance insureds. We have compiled the various pamphlets that give an overview of the coverage offerings and include FAQs. The information provided is a general product summary of the resources and should not be construed as a guarantee of coverage.
To access these resources, please contact your Business Development representative.

This pamphlet provides an overview of the available resources ProAssurance’s insured physicians can use to protect themselves against risk associated with rising cyber threats. Some of the resources include PCI DSS Assessment, Multimedia Liability, and Cyber Extortion. A brief summary with general description of each of these are included in the piece.
Similar to the CyberAssurance Plus resource for Physician Practices, this pamphlet provides a brief overview of ProAssurance resources for cyber liability insurance for hospitals and healthcare facilities. Also included is a list of states where this type of coverage is unavailable, including Arkansas, Kansas, Minnesota, and South Dakota.
CyberAssurance Plus Flyer (For Hospitals & Healthcare Facilities Only).

This flyer explains how ProSecure acts as an extension of CyberAssurance Plus by providing physician practices, hospitals, and healthcare facilities with higher cyber liability limits plus coverage for regulatory risk protection. The types of coverage, a breakdown of first-party insuring agreements, and a description of regulatory risk protection coverage are included.
ProSecure Flyer for Physician, Hospitals, & Healthcare Facilities.
This material provides theoretical situations that showcase the potential benefits of enhanced cyber liability coverage via CyberAssurance Plus and ProSecure. There are circumstances in which the Regulatory Risk Protection Coverage provided by ProAssurance may also be used. Some of the scenarios include handling a hacker who used malware to attack a physician’s computer system; using a new automatic telephone dialing system that introduced potentially unsolicited or unauthorized calls; and managing audits from the Centers for Medicare & Medicaid Services or a civil investigation from the U.S. Attorney’s Office.
This resource provides common questions and answers from ProAssurance agency partners concerning ProSecure. Some of the queries include “What is ProSecure?” and “Is ProSecure available to any agent?” Also included is contact information for both ProAssurance and Tokio Marine HCC to address any additional questions that may arise.

When a major crisis happens to your business, how you respond can go a long way toward saving or sinking your reputation among your clients and the public. A data breach, in particular, is a difficult crisis to manage since it involves technical (and often legal) aspects that smaller organizations may have little formal knowledge of. These events can be so complex and multi-layered that even large global enterprises have difficulty managing them.
Among the largest and highest profile data breaches was the 2017 Equifax data breach. The company’s widely-criticized response to the crisis has been called “a masterclass in bad crisis management” and “haphazard and ill-conceived,” so much so that security and communications experts are still dissecting the company’s response years later. The potential of experiencing a devastating, complex crisis like this makes proactive response planning critical.
The Challenges of Responding to a Data Breach
In a crisis like a data breach—especially if it involves personnel or financial records—your business will face technical, legal, regulatory, and reputational challenges, each involving very different functions within your organization. An effective response requires coordination among many disparate elements: security, legal, HR, IT, communications, and often external organizations and third-party partners. This is not the time for silos.
The Technical Challenge
There are any number of ways a data breach can happen, some nefarious (a criminal hacking into your system or a disgruntled employee downloading data to sell), others accidental (a lost laptop). The first step after discovering a data beach is determining what happened. Losing a laptop containing a few dozen records is serious but warrants an entirely different response than a criminal hacker exfiltrating your customer database and selling it on the dark web.
Determining what happened often requires technical knowledge and forensic skills that smaller businesses don’t have among their staff. If your IT contractor or staff are unable to quickly discover the source of the breach, you might consider hiring a cybersecurity incident response service. A reputable one may also be able to assist in the legal aspects of your response and help develop a communications plan. Consult with your business attorney or cyber liability insurance carrier for recommendations.
The Legal Challenge
Whether it’s the loss of client financial information or personnel files, a data breach that includes sensitive personal data will likely trigger legal obligations. These may include FTC and state-level compliance reporting, notifications to affected individuals, and ultimately may require litigation defense. It’s a good idea to contact your business attorney to help assess these challenges before communicating with affected individuals or making public announcements.
The Reputational Challenge
When your clients provide you with the sensitive financial and personal information you need to deliver your services, they entrust you to maintain its privacy and security. When that information is compromised, it’s not just a breach of data but a breach of trust. If you have a good reputation among your clients and your community, they are more likely to be forgiving of a data breach. But if you fail to respond transparently, helpfully, and diligently to address the problem, that good will could wane.1
CRISIS COMMUNICATIONS BEST PRACTICES
A data breach is not just a crisis for your business, it’s also a crisis for the affected individuals and their families who had sensitive details about their lives exposed in ways that could negatively impact their personal and financial lives. This principle should be the “North Star” that guides your efforts. How well you do that in the aftermath of a breach could affect how your reputation survives the crisis. Businesses today should take heed of the lessons learned since Equifax’s well-publicized stumbles and other breaches to help prevent the further erosion of trust and accelerate the rebuilding of your reputation.
Communicate what you know and can confirm as soon as you can without unwarranted delay.1 The more you delay your response, the more you’ll appear to be stalling.1 Be as transparent and as open as it is prudent to be, and put your organization’s leadership front and center. A siege mentality where you hunker down and close ranks may be an instinctual reaction to a crisis but, with your public reputation at risk, it’s not a wise one. Hiding behind vague legal statements and not answering questions will make you appear evasive.1
Being transparent doesn’t mean being hasty. Share only confirmed information without speculation about causes or motivations, and without promises you can’t guarantee. Given the regulatory and legal implications of a data breach, your legal team should be a close partner in drafting and approving every public statement.2 Be cautious about reporting hard information such as numbers of records before the investigation is complete. Releasing specific but unconfirmed details too early may lead to backtracking later if the information changes. This could lead to confusion or be seen by customers and observers as an attempt to change the narrative.2,3 Seek outside legal counsel or crisis management consultants to assist if needed.2
In communicating with affected individuals, be as open with information as you can within the guidance your legal team provides and try to anticipate their questions. Focus on how the breach affects them and what you’re doing about it. If certain information can’t be shared (for example, details of an ongoing law enforcement investigation), explain those reasons clearly.3 Avoid even the hint of any strings attached to services you offer to affected individuals. If, for example, you offer free credit monitoring but make it a trial requiring a credit card for activation or sneak a forced arbitration clause into the fine print, your attempted goodwill likely lead to more outrage, as Equifax discovered.1
Prior to your public announcement, brief your social media team to halt social media posting and turn off all scheduled or programmed posts until a communications plan is in place.1 A harmless social media post scheduled before the breach could be horribly uncomfortable post-breach. Equifax learned this the hard way when a likely unaware customer service employee tweeted “Happy Friday!” the morning of the breach announcement. Be deliberate and coordinated in your communications on all channels to prevent embarrassing stumbles that become their own mini-crisis. Prepare your social media and customer support teams with the information they need to address questions they receive.2 You can restart posting when the time is right with legally approved messaging and links to published communications.
A data breach is a devastating event for a business and the affected individuals and can lead to reputational harm to your business. But, with a properly managed response, you can restore your reputation and earn back the trust of your clients and community.
1. John F. Fitzpatrick, “Equifax Scores a Failed Rating for Crisis Communications,” Stratacomm, September 8, 2017.
2. Ashley Sawatsky, “What’s the Best Way to Communicate After a Data Breach?” Dark Reading, December 20, 2023.
3. Cody Chamberlain, “The Do’s and Don’ts of Communicating a Data Breach,” Security, May 23, 2022.
.png?width=300&name=MicrosoftTeams-image%20(28).png)
According to the company’s website, CrowdStrike is used on more than 1 million individual devices in healthcare organizations throughout the United States. The outage affected many hospitals and health systems. According to the American Hospital Association, the effects of the outage varied, and the health systems hit hardest activated backup plans and adjusted workflows while IT systems were manually restored. (Advisory Board)
Cybersecurity firm Recorded Future counted 44 healthcare-related incidents in the month after Change Healthcare’s payment came to light—the most it’s ever seen in a single month. (Wired)
The U.S. Department of Justice accuses North Korean national Rim Jong Hyok of working for the country’s military intelligence agency that uses cyberattacks against healthcare providers to collect ransoms to fund more attacks against U.S. government agencies, according to the indictment filed in the U.S. District Court for the District of Kansas. (Fierce Healthcare)
The White House has tapped Microsoft and Google to provide free cybersecurity services to approximately 2,000 “critical access” hospitals in an effort to protect healthcare in rural parts of the U.S. Critical access facilities are located more than 35 miles from comparable facilities, making their continuous operation essential to residents and their need for security funding, assessments, tools, and training great. (FedTech)
Hackers are using phishing schemes to steal login credentials, enabling unauthorized access and diversion of automated clearing house (ACH) payments to U.S.-controlled bank accounts. These attacks often begin with hackers gaining access to employees’ email accounts through social engineering or phishing. Once access is gained, they specifically target login information related to reimbursement payments for insurance companies and Medicare. (Becker’s Hospital Review)

How I Used Referrals to Build My Medical Sales Career

Everyone who sells to healthcare quickly discovers that getting time with medical professionals is challenging, especially when they don’t know you.
My medical sales career began by circumstance. I was a nuclear medicine technologist working for a start-up that offered mobile clinical services. After months of setting up the business, we needed customers.
My boss interviewed several experienced salespeople, only to scoff at their salary demands. “Let me do it,” I said. “I’ve spent most of my working life talking to doctors.”
He allowed me to give it a try.
I created a list of physician prospects and began cold-calling by telephone and in person. Every receptionist responded to my efforts with the same script: “You can leave information, and the doctor will call you if they’re interested.”
After weeks without a callback, I went to the boss. “I can’t get in a single door. Do you have any ideas?”
He said, “Let’s call Dr. Ken.” Dr. Ken was a local radiologist who would be reading our nuclear medicine scans.
When Dr. Ken and I met, he asked, “Who are you trying to see?” I handed him my list of physician prospects. Grabbing a pen, he checked off names. “I’ll call the doctors I know and ask them to meet with you. When you go to their office, tell them Dr. Ken referred you.”
I waited a few days and got on the phone. “I’m calling on behalf of Dr. Ken to schedule a business meeting with Dr. X. He’s expecting my call.” I got the appointment on the spot or was notified of one within a day or two. Thanks to Dr. Ken’s referrals, the business was up and running.
Rediscovering Referrals
After a small taste of sales success, I left nuclear medicine for orthopedic implant sales. This required selling to orthopedic surgeons, who tend to be highly averse to changing implant systems. I struggled to access many of them since they didn’t know me.
One day, a new customer, Dr. Jeffries, asked if I had done any business with Dr. Charles, a local surgeon he had trained with. I responded, “His receptionist says he won’t meet with me because he’s happy with his current supplier.”
Dr. Jeffries offered to call his friend on my behalf and put in a good word. The next time I visited Dr. Charles’s office, he invited me in and treated me like an old friend.
I got into the habit of asking doctors I knew for introductions to their sales-resistant colleagues. It was as simple as, “Do you know Dr. Smith? Would you be comfortable introducing me? And if you’re not comfortable, I fully understand.” It helped me build relationships and business much faster than I could on my own.
A Different Type of Referral
One of my surgeons asked me to sponsor and attend one of the county medical society’s monthly meetings. During the meeting, the president touted the society’s value as a patient referral source for its members. I jokingly asked the administrator, “What about sales reps? Can I tell doctors that I was referred by the county medical society?”
She said, “Of course. As a supporter, you have my blessings.”
So I gave it a shot. “I’m calling on behalf of the county medical society for Dr. X.” While it wasn’t as effective as a personal referral, I was amazed at how often it succeeded.
If you ever struggle to access physicians or other healthcare prospects, find a credible referral source. Referrals bestow trust, foster relationships, and get you to the sale faster.

|
Written by Mace Horoff of Medical Sales Performance. Mace Horoff is a representative of Sales Pilot. He helps sales teams and individual representatives who sell medical devices, pharmaceuticals, biotechnology, healthcare services, and other healthcare-related products to sell more and earn more by employing a specialized healthcare system. Have a topic you’d like to see covered? Email your suggestions to AskMarketing@ProAssurance.com. |
ProAssurance Officially Accredited with Two-Year Provisional Accreditation
ProAssurance recently received its provisional accreditation from the Accreditation Council for Continuing Medical Education (ACCME). ProAssurance achieved this accreditation by using current educational activities that demonstrate compliance in the areas reviewed by the ACCME. Risk Management will revise available programs and publications carrying continuing medical education (CME) credits to reflect the updated ACCME accreditation statement identifying ProAssurance as the accrediting body. The accreditation statement must appear on all CME activity materials and brochures distributed by ProAssurance.
Previously, ProAssurance Indemnity Company, Inc. was ACCME accredited from 1995 to August 2021. NORCAL Insurance Company officially joined the ProAssurance Group of companies in May 2021, and in July 2021, NORCAL received ACCME Accreditation with Commendation. Due to the timing of program expirations and reaccreditations, the two companies came together in August 2021 to provide accredited CME through joint providership with the NORCAL Accreditation with Commendation achievement. As integration continued, it was decided that now was the time to begin the 12-month process of returning to a ProAssurance ACCME accredited education program. This provisional accreditation is current from July 22, 2024 to July 31, 2026, at which time ProAssurance will apply for full accreditation.
ProAssurance recognizes the time and effort of the CME team, with a special thanks to Shirley Armenta, the CME Administrator, for accomplishing this task. ProAssurance is committed to continuing to provide applicable, timely, and innovative continuing medical education to our policyholders and partners.







